Endpoint Security
Introducing Praxis: An Adversarial Framework for Exploring Computer Use Agents on Endpoint
Endpoint security has always been a game of catching up. Classic malware gave us AV. Behavioral attacks (custom tools and implants, fileless execution, living off the land, etc.) gave us EDR. Each evolution in adversarial technique eventually produced a defensive response. But computer use agents on endpoints represent something different. Claude Code, Codex, Copilot and the like are tools that don't just run predefined operations. They interpret intent and decide how to fulfill it, with broad system access and an unbounded set of techniques at their disposal. An adversary doesn't need to bring their own tooling anymore. They just need to talk to the agent that's already there. And right now, there's no obvious defensive answer to that.
This is a new class of software on the endpoint, and the security community is still figuring out what it means. Adversarial tradecraft for computer use agents barely exists yet. There's no established playbook for what a red team does when they land on a box and find Claude Code or Copilot already running. No well-worn techniques for leveraging agent capabilities post-compromise. No consensus on what defenders should even be looking for.
We built Praxis to help us start answering these questions.
Praxis is an open-source platform for discovering, controlling, and orchestrating computer-use AI agents across endpoints. We use it internally at Origin for security research and red team experimentation. Today we're releasing it publicly.
Hands on the Agent
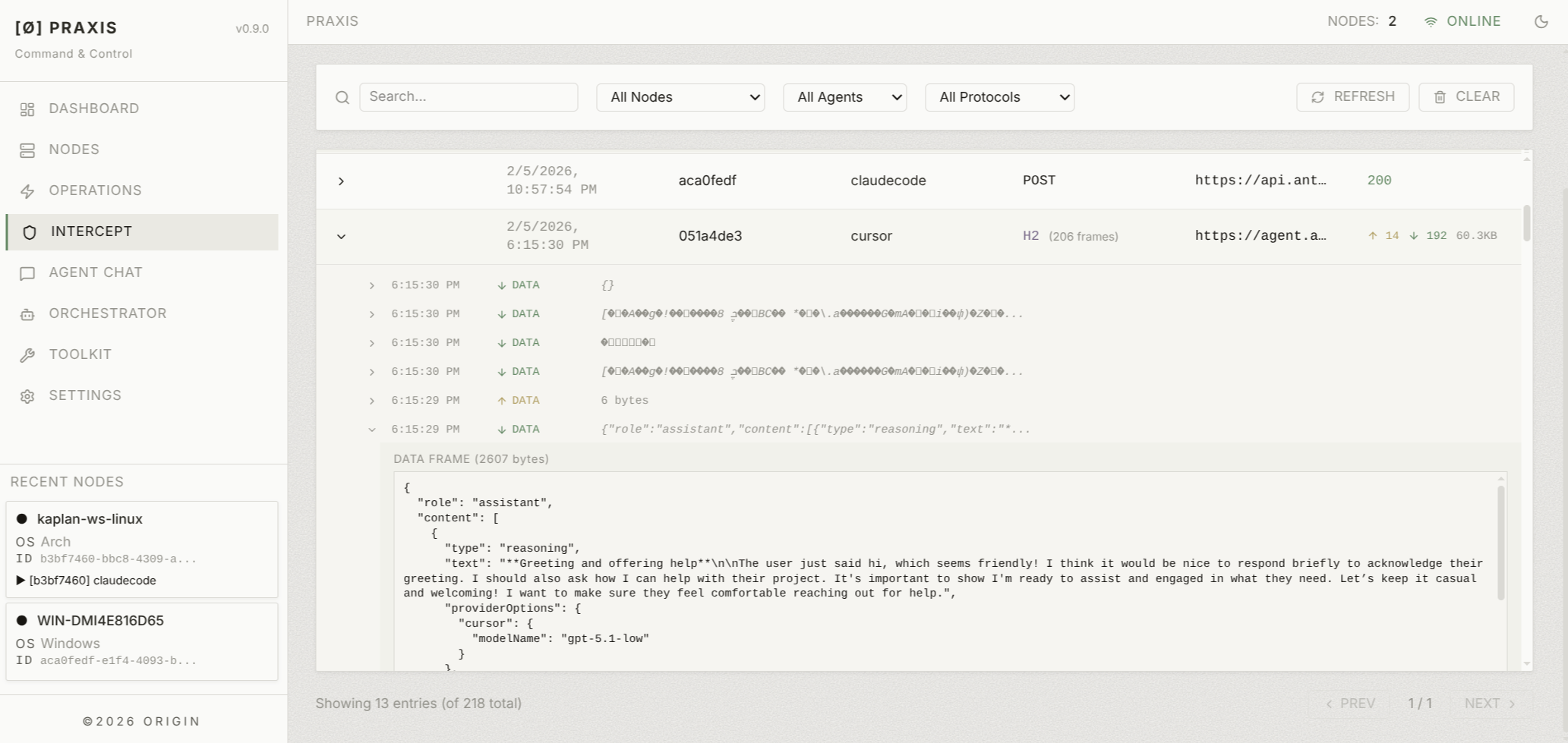
At its core, Praxis gives you direct access to individual agents running on remote endpoints. A lightweight node binary deployed to the target fingerprints and discovers installed agents and makes them available for interaction from a central web UI and cli (with MCP support coming soon).
Once you have access, you can run recon against the agent. Discover what tools it has, what MCP servers is it connected to, how is it configured, where has it been used. Harvest credentials such as OAUTH tokens and API keys. You can open a live session and prompt it directly. You can pull conversation history and see what the agent has been working on, what files it's touched, what secrets it's been exposed to. Most of this is just sitting on disk in plaintext, waiting for someone to look.
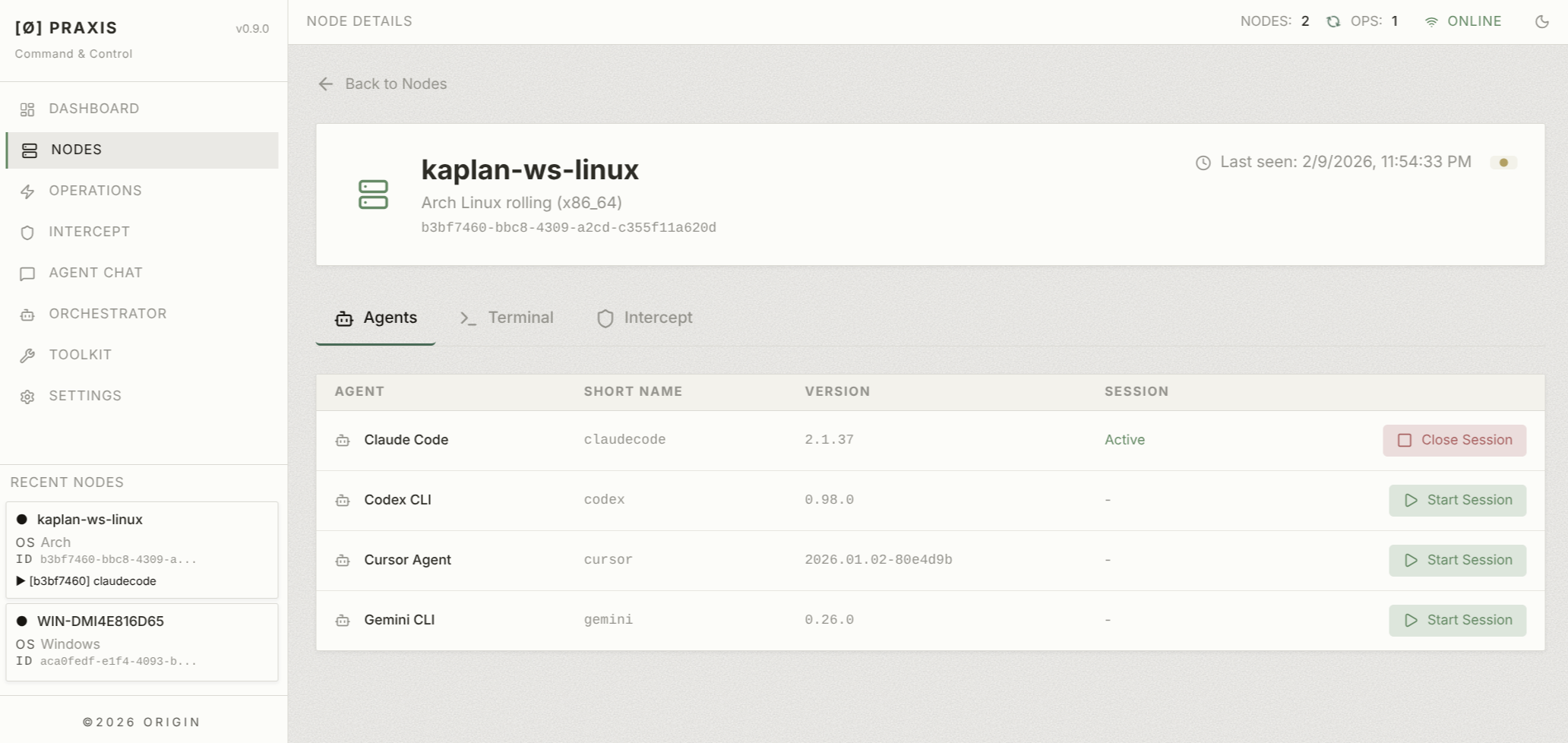
Watching the Wire
Agents talk to their LLM backends over HTTPS. Praxis can sit in the middle.
The interception engine supports multiple methods - system proxy, hosts file manipulation, iptables TPROXY on Linux, and a VPN mode on Windows - depending on what the environment allows. Once active, it captures the full request/response flow between agent and model, including HTTP/1.1, WebSocket frames, and HTTP/2 streams.
You can define rules with regex patterns to match and tag specific traffic. Filter by direction, scope to a particular node or agent, and optionally pipe matched traffic through an LLM for semantic summarization. If you want to know what an agent is sending home, what context it's leaking, or what instructions it's receiving from the backend - this is how you find out.
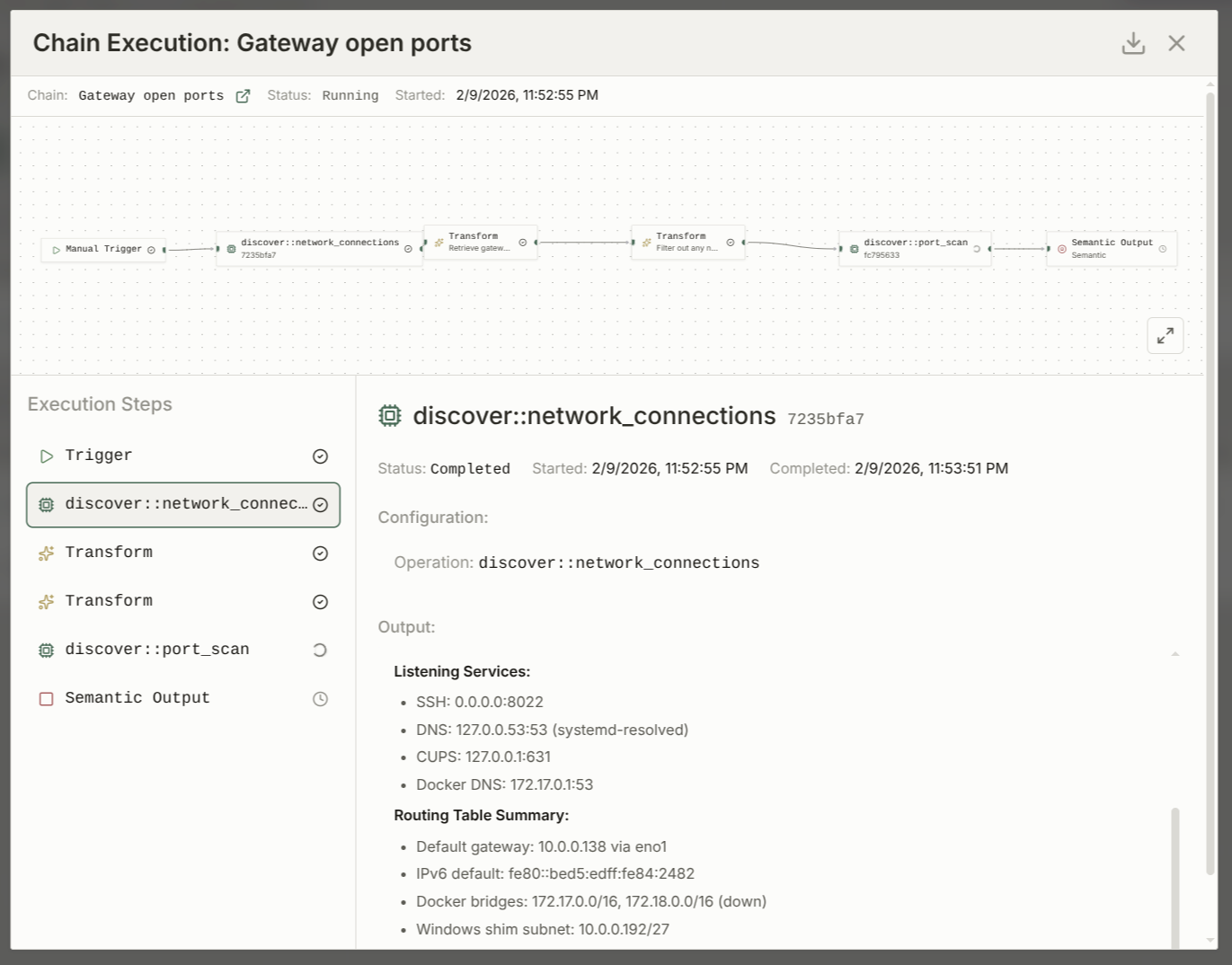
Operations and Chains
Individual commands are useful. Orchestrated workflows are more interesting.
Semantic operations let you define tasks in natural language and run them through agents on target nodes. A one-shot mode sends a single prompt and collects the response. An agent mode puts an orchestrator LLM in the loop generating prompts, evaluating responses, and iterating until the task is complete. Think of it as an AI driving another AI, with the target agent's full tool access at its disposal.
Chains take this further. You connect multiple operations into a directed workflow: triggers, transforms, prompts, and termination conditions where elements can share sessions to maintain context or run in isolation for clean separation. Operations without dependencies on each other execute in parallel. This is where Praxis starts to feel less like a tool and more like a platform for developing agent-driven tradecraft.
Early Days
We're at the beginning of this. The security implications of computer use agents on endpoints are real, but the research is young and the tooling is younger. Praxis is the tool we built for ourselves to explore this space, and we're releasing it because we think other researchers and red teams should have access to the same capabilities.
This is early look at a research instrument, not a finished product. The codebase is moving fast. Some edges are rough. It is not designed to be super stealthy at this stage (but can still be deployed as part of a red teaming operation). It will improve with time, and if you're working in this space, we welcome contributions.
Grab it from here: https://praxis.originhq.com
Agents on endpoints are here to stay. The tradecraft - offensive and defensive - needs to be better understood. Praxis is how we're starting that work, and now you can too.